Are you fully covered for PCI DSS 4.0?
PCI DSS 4.0 adds new requirements related to vulnerability scanning authentication, asset classification, file access management, cloud security, and much more. Are you ready? Qualys can help.
Qualys TruRisk Platform in numbers
8+ trillion
5+ billion
2+ trillion
20+ apps
6+ billion
99.9996%
All your data analyzed in real time
Respond to threats immediately

See the result in one place, in seconds
Qualys TruRisk Platform is accessible directly in the browser, no plugins necessary. And with a powerful dashboard, security and compliance pros and managers get a complete and continuously updated view of all of their IT assets — from a single-pane-of-glass interface.
It’s a fully customizable dashboard that lets you see the big picture, drill down into details, and generate reports for teammates and auditors. Its intuitive and easy-to-build dynamic dashboards aggregate and correlate all of your IT, security and compliance data in one place from all the various Qualys Cloud Apps. With its powerful Elasticsearch clusters, you can now search for any asset – including on-premises, endpoint and cloud assets – with 2-second visibility
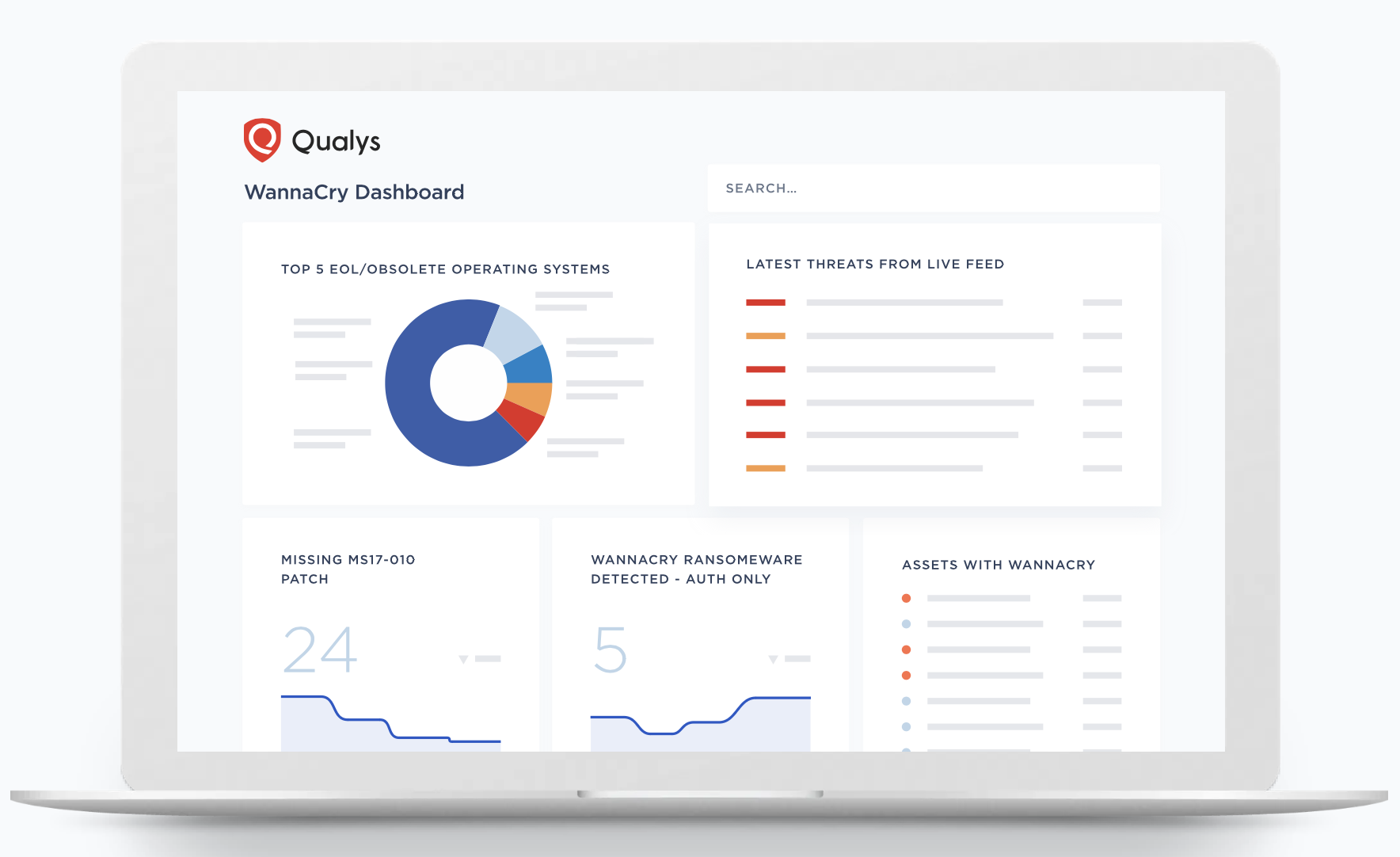
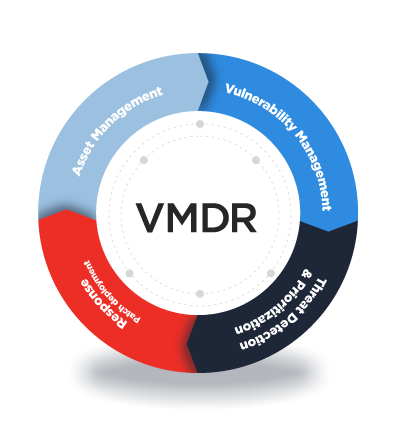
Qualys Vulnerability Management (VMDR)
Redefining Cyber Risk Management
Cyber risk is business risk – with risks growing faster than what traditional VM and SIEM tools can manage. Security and IT teams need a new approach to tackle cyber threats with a clear understanding of cybersecurity risk and automate workflows for rapid response.
Extend Compliance Coverage from VMDR
- Create compliance dashboards to highlight compliance gaps and provide pre-built templates, profiles, and policies to achieve full compliance.
- Measure, communicate, and eliminate cyber risk across the global hybrid IT environment.
- Clearly report and articulate risk to internal and external compliance stakeholders across 950 policies, 20,000 controls, and 100 regulations.
The Qualys Cloud Platform simplifies the complexity associated with managing multiple security solutions, while at the same time increasing the automation, effectiveness and proactive nature of security.